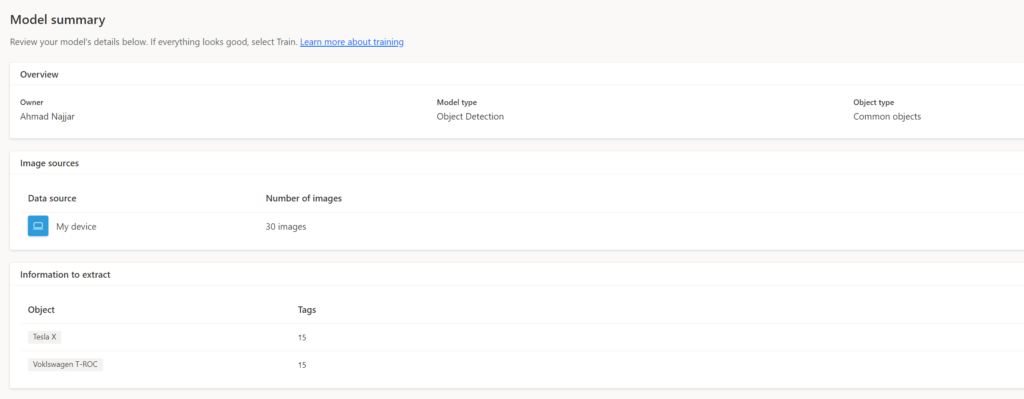
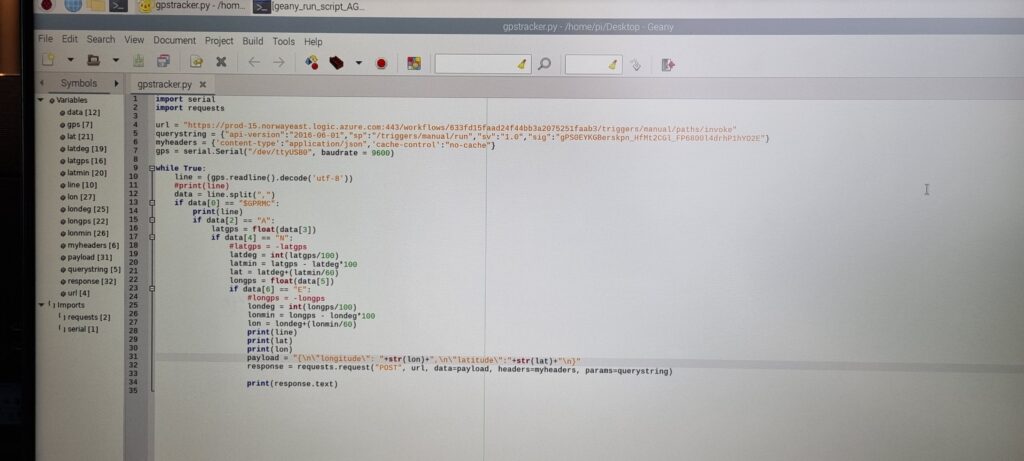
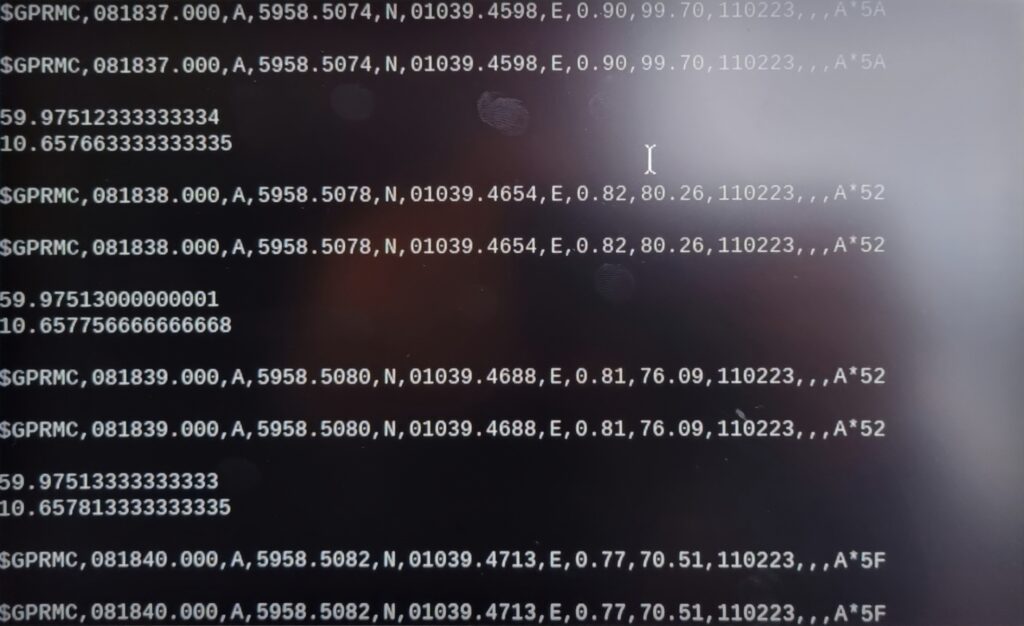
PERP is an ERP system(s) made easier for Pirates and for the mass. It is built from 4 subsystems.
PFM – Pirate Fleet Management
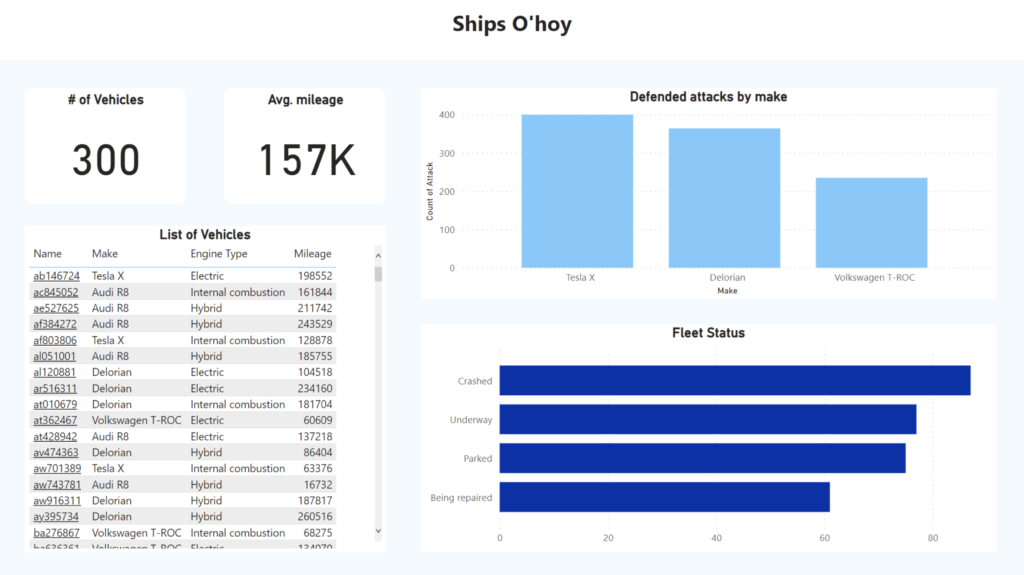
Management of pirates vehicles fleet. It involves the coordination and management of all activities related to vehicles, including enlisting, licensing, deployment (for looting), and tracking.
POM – Pirate Operations Management
Managing the various tasks and processes involved in pirating. This is where the leaders of the organisation can make intelligent data driven decisions and engage their fleet with looting.
PRS – Pirate Reporting System
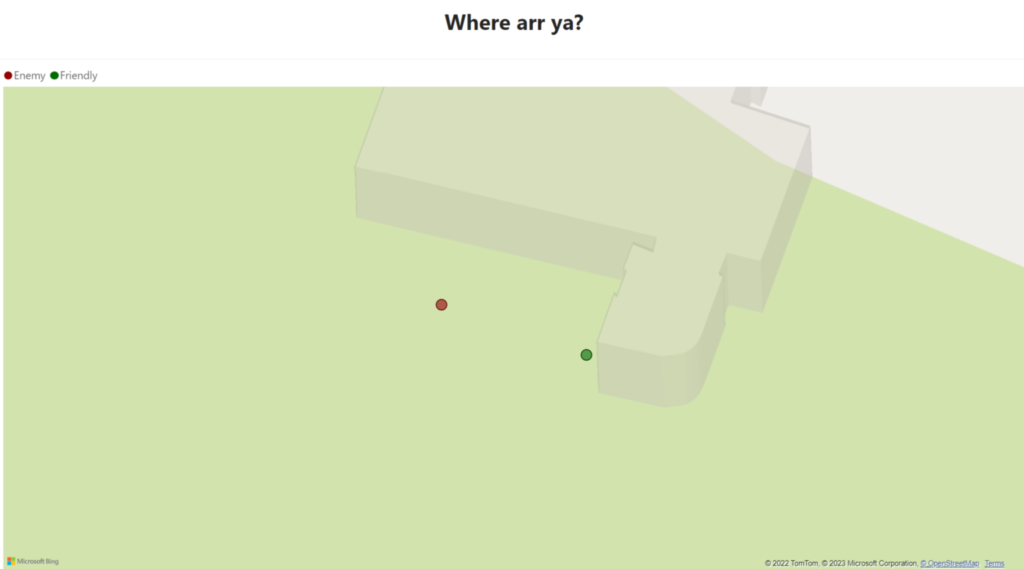
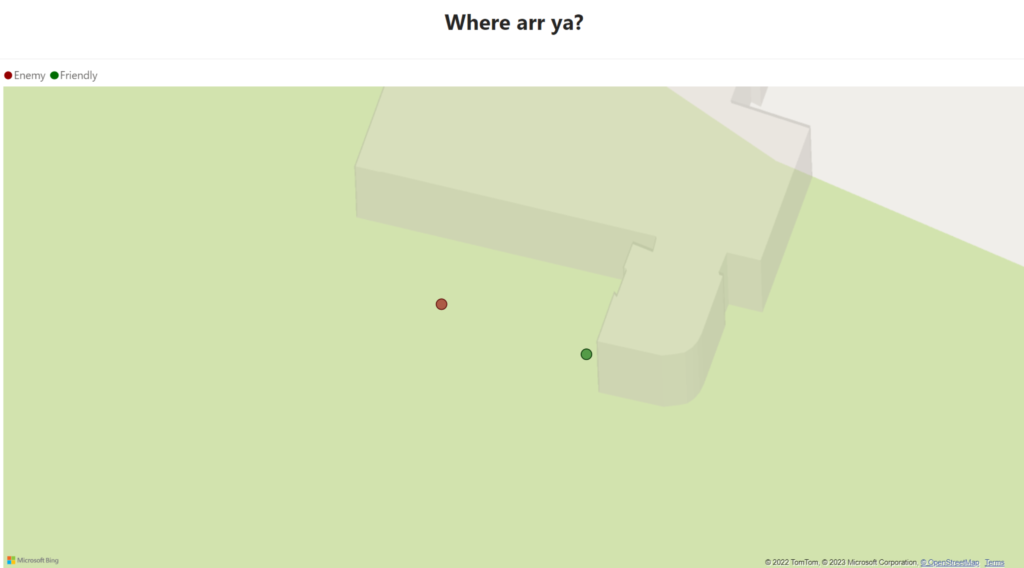
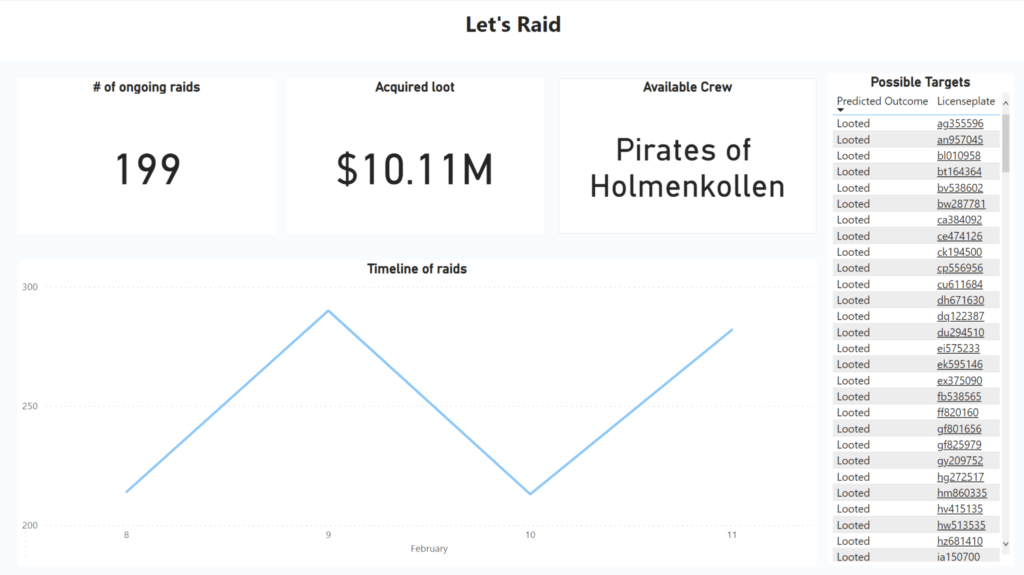
Covers different reporting needs such as live location reporting of pirates, enemies and loot (target) locations, as well as vehicle, pirate statistics as well as reports on previous raids. It also includes the results of our predictive models to be able to visually see which targets would be best to attack.
PRM – Pirate Resource Management (HR)
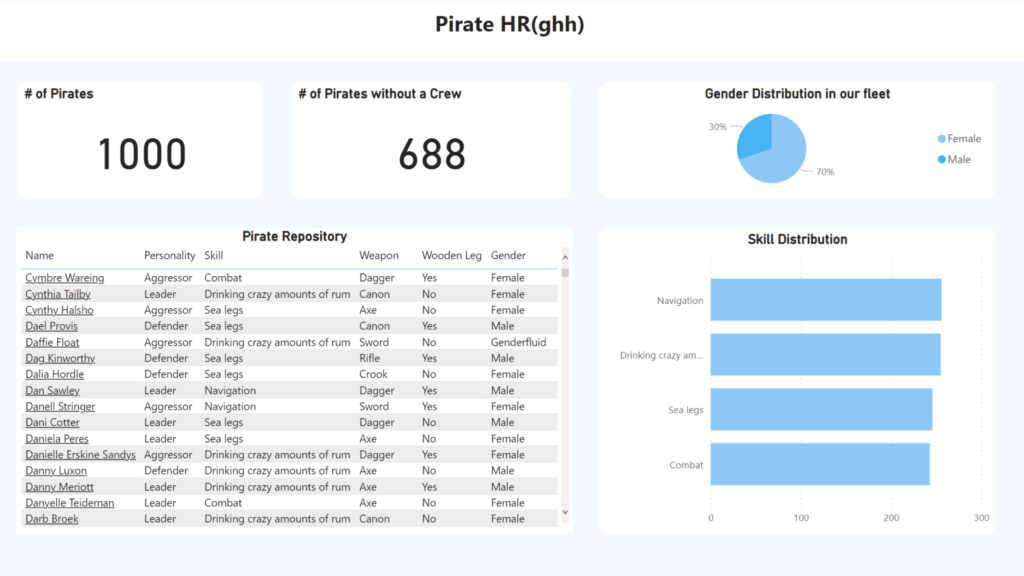
The system helps in automating and streamlining pirates’ processes, such as recruiting, onboarding and performance management. The goal is to increase efficiency and reduce manual labor, as well as provide a single source of truth for employee data and records. It stores information regarding skills, pirates in their crews, new hires and gender distribution.
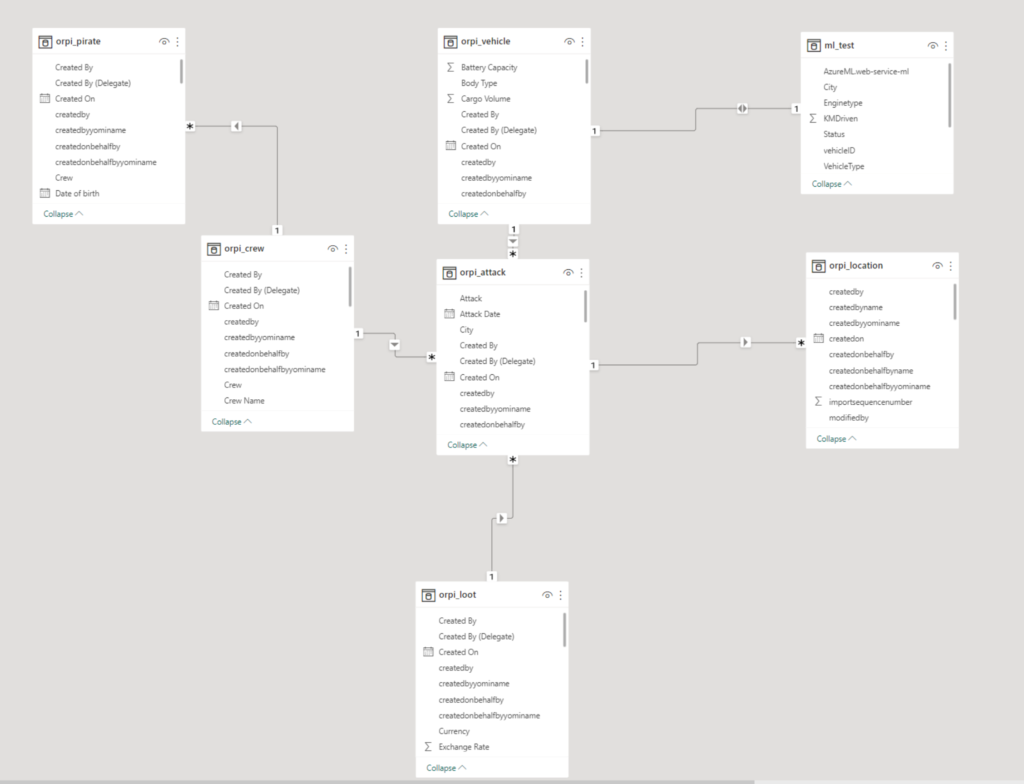
Application Workflows
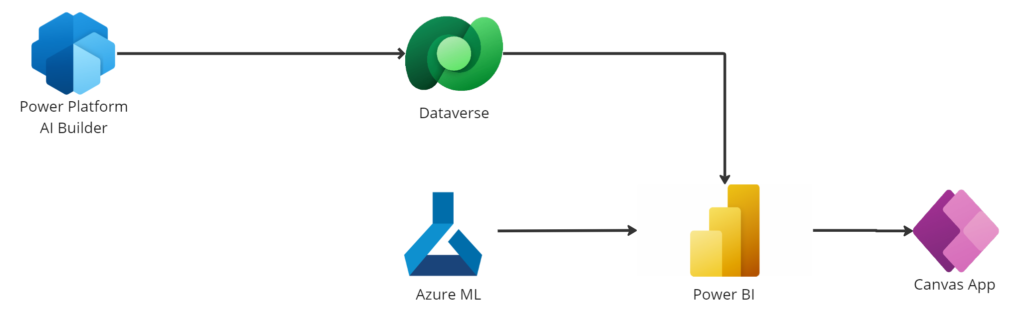
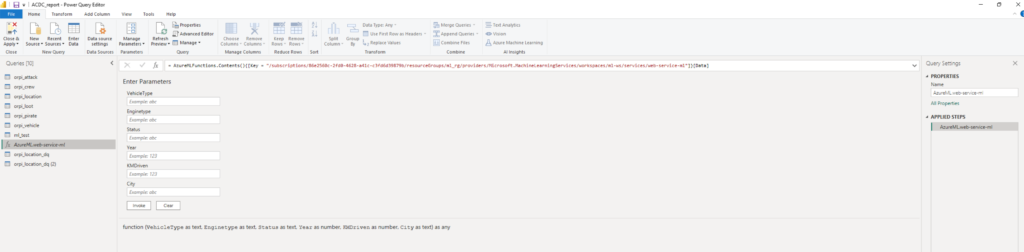
For the reporting layer we gather data from different sources such as AI Builder outputs which again is getting info from Statens Vegvesen. This data as sent to Dataverse which is then collected from Power BI via the Dataverse Connector.
We also have an Azure AutoML classification model which we are calling from Power BI to do predictive analytics on incoming vehicle data. All these sources are the basis of our reporting in Power BI and hence, contributes to make well informed, data driven decisions for the captains in our fleet.
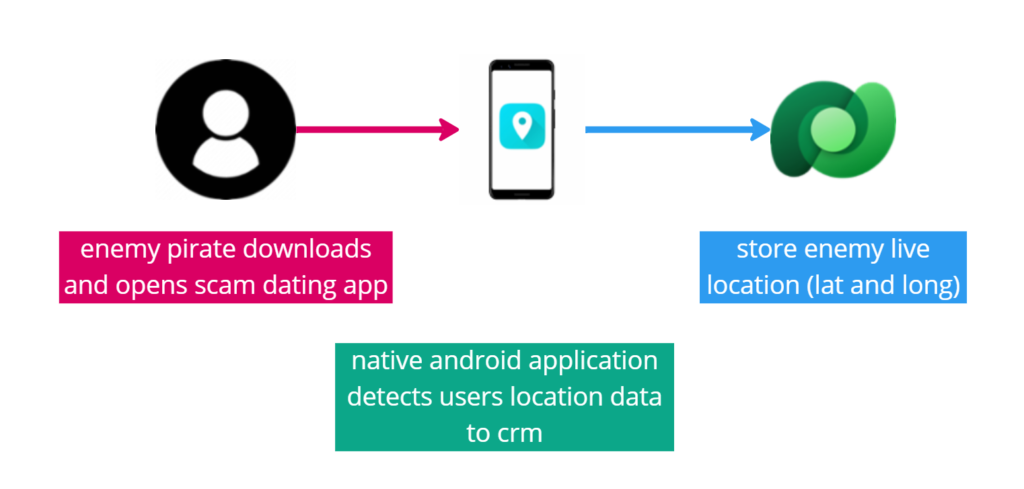
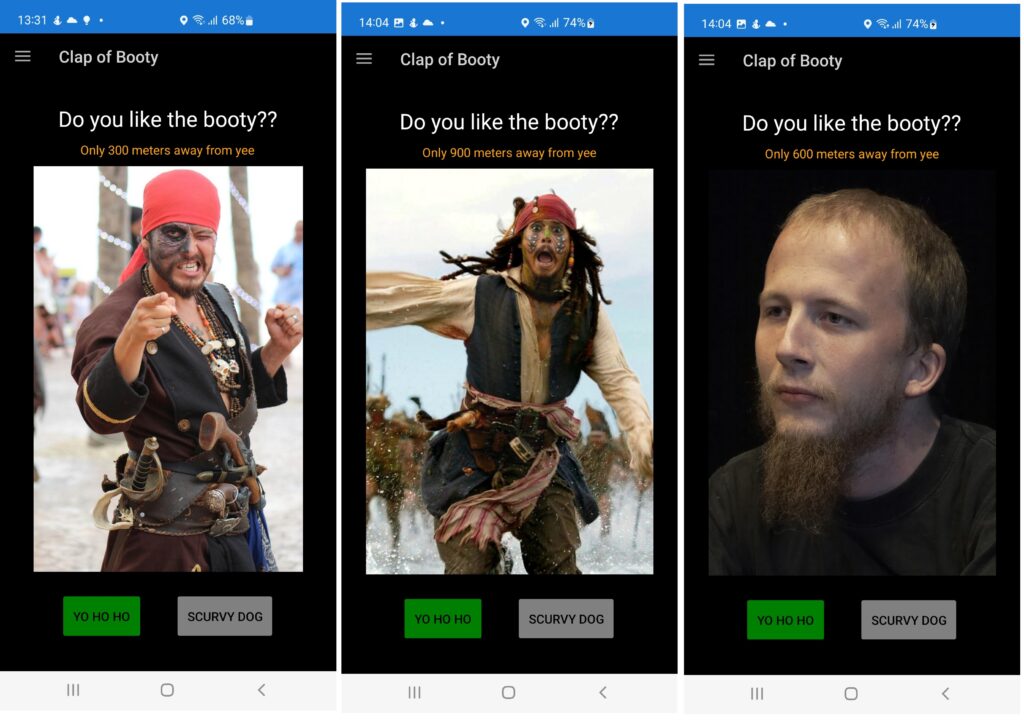
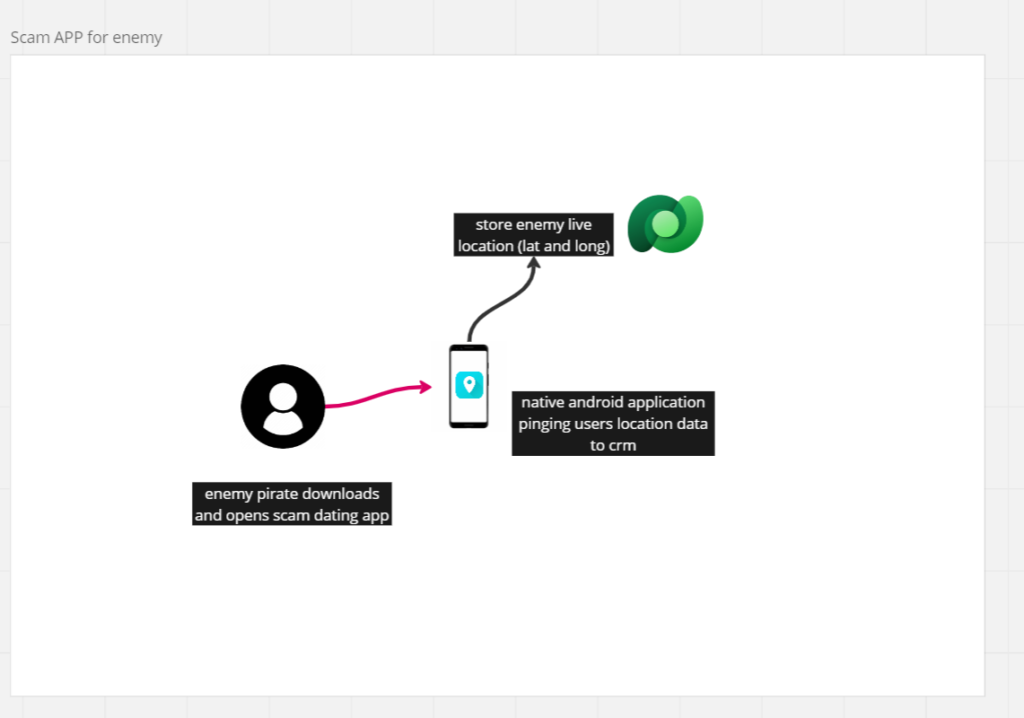
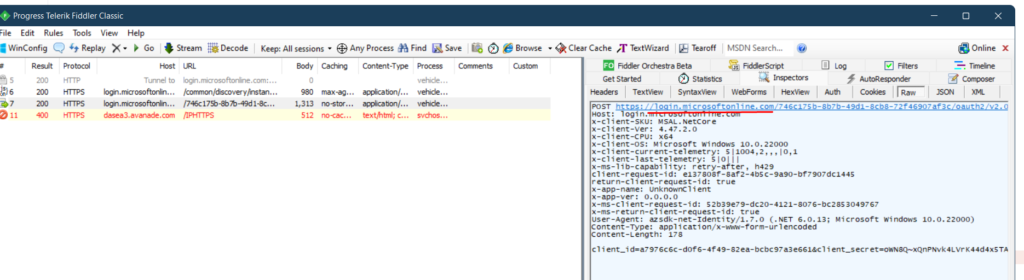
In this workflow, we describe the how the process of aquiring enemies live location is done.
By tricking the enemy into thinking they downloaded a dating app, we are actually pinging their location and storing it in our CRM system.
Technical:
App is a native android app developed in Xamarin. Location report is done once every 5 seconds and it contains users Latitude and Longitude.
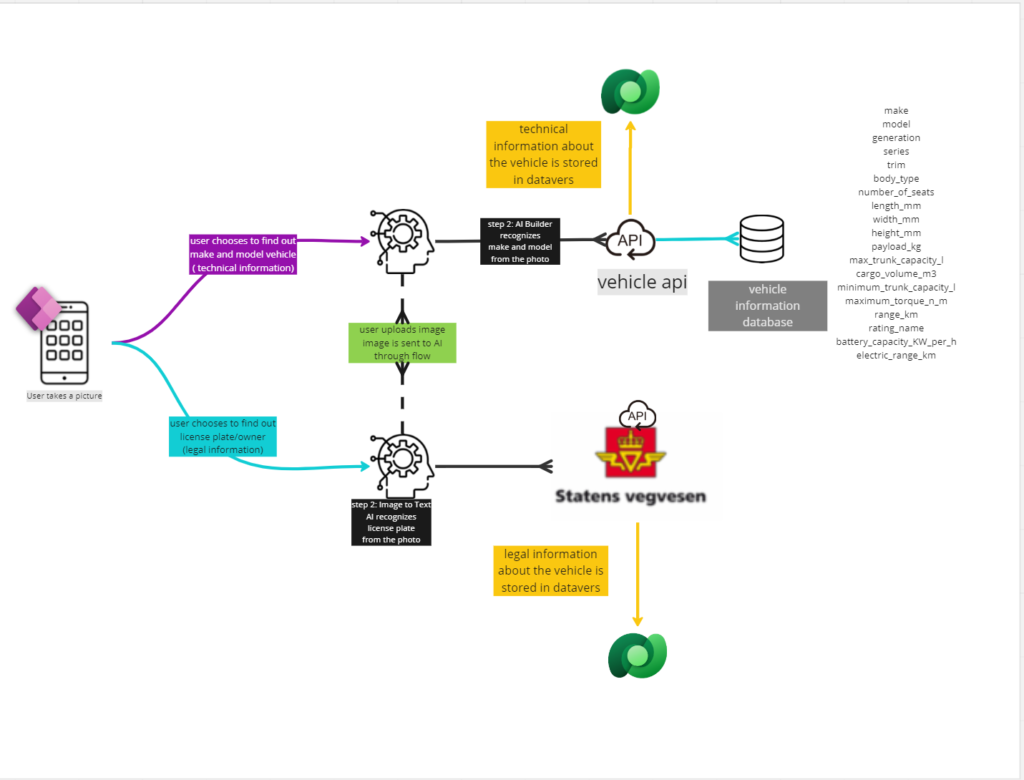
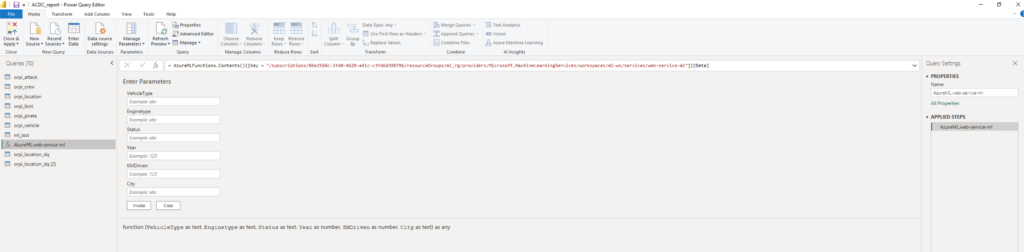
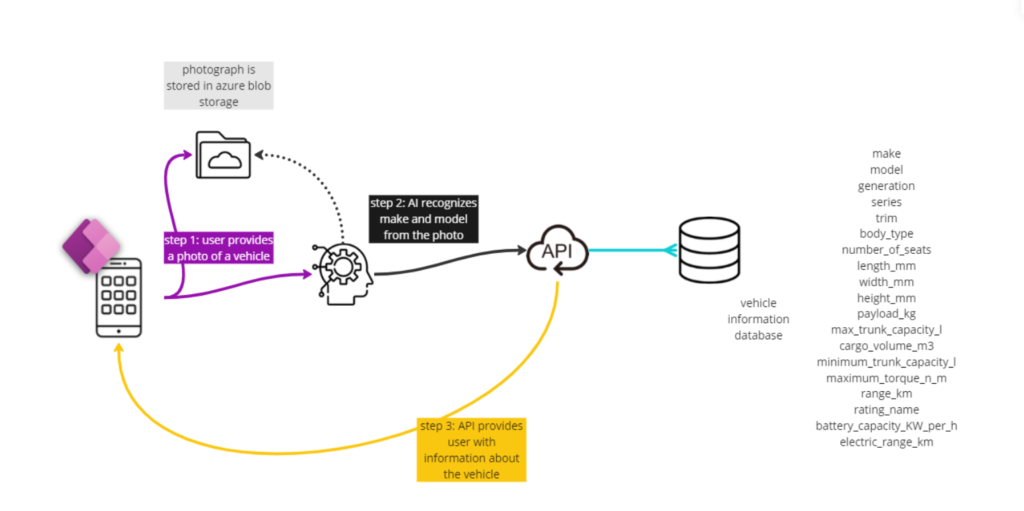
In this workflow, we describe how we enlist vehicles to our fleet. User opens the Canvas Application and takes a photo of possible addition to fleet vehicle. Using Azure Machine Learning, we identify make and model of the vehicle. These two datapoints are sent to an Azure API which is on top of Technical Vehicle Database that contains technical information about the vehicle.
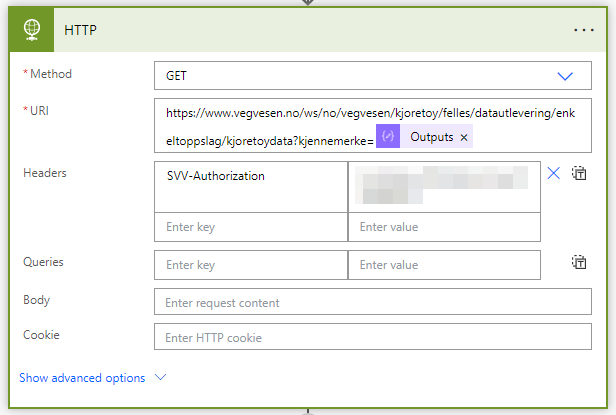
Using another Azure Machine Learning algorithm we recognize the license plate of the vehicle. The license plate is sent to Statens Vegvesen API to retrieve the legal information about the vehicle.
Both datasets (technical information and legal information) is then shown to the user of the canvas app and he decides to store them in the CRM.
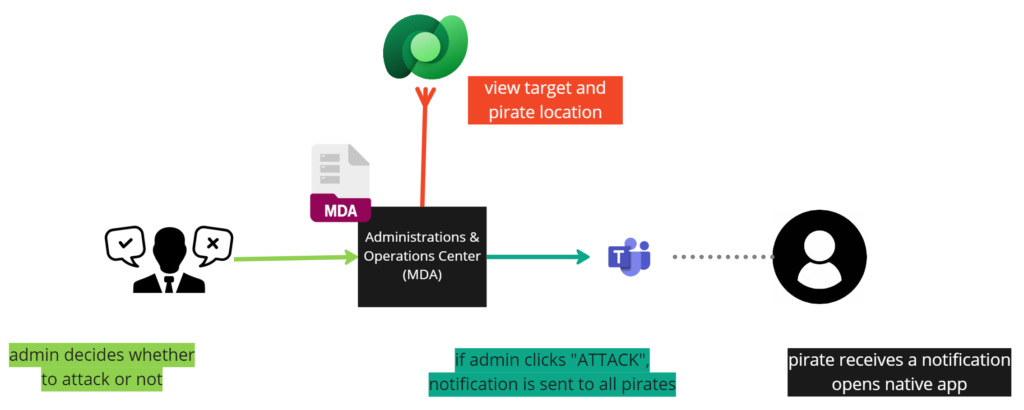
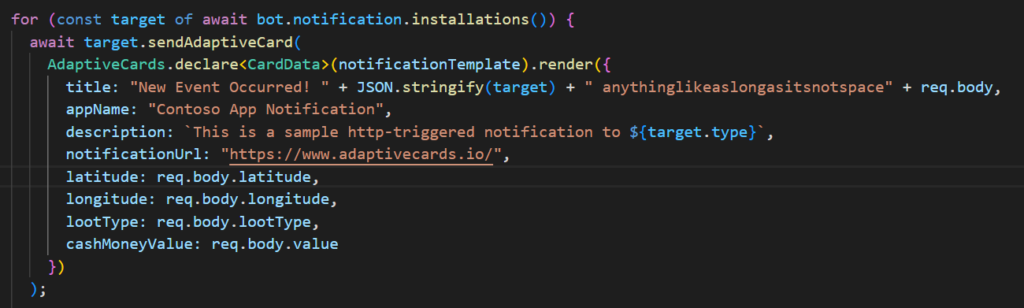
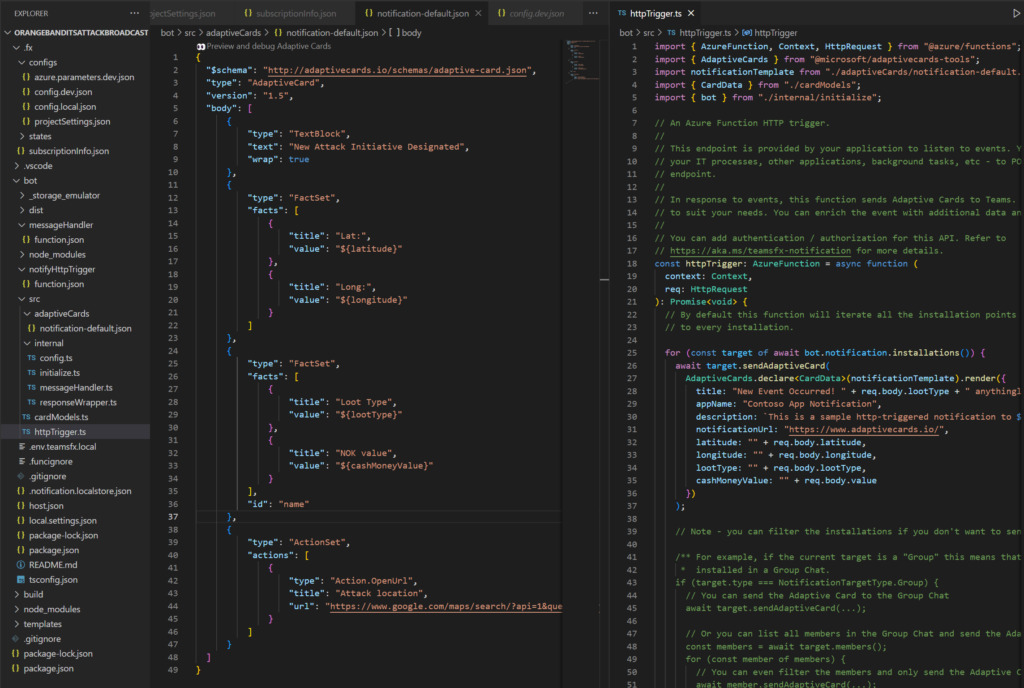
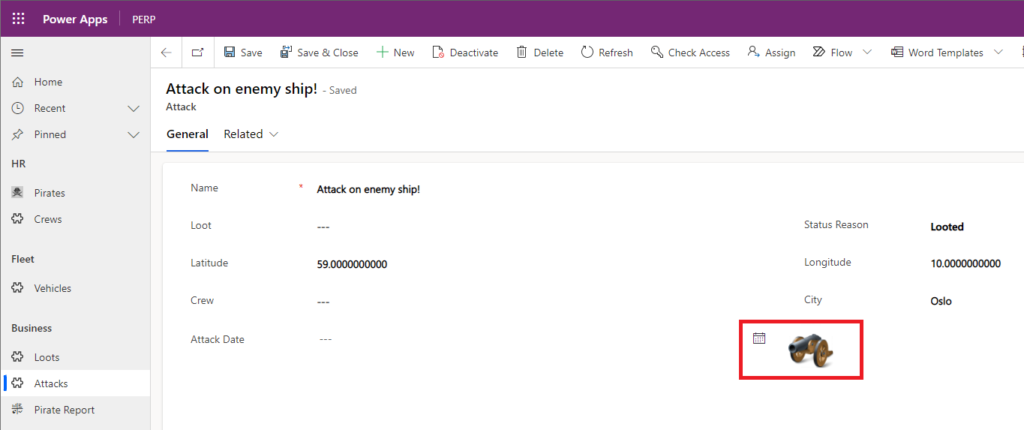
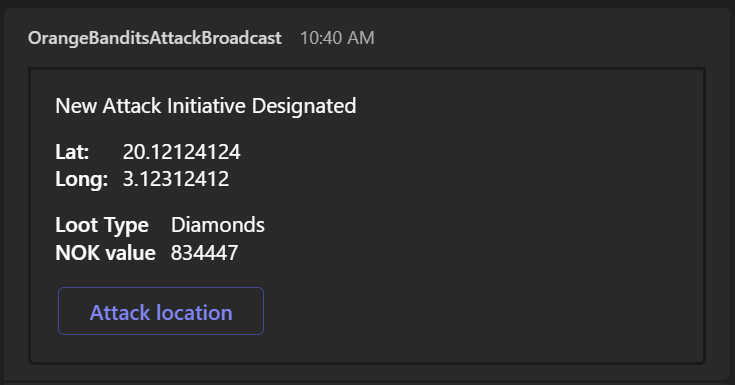
In this workflow, we describe how friendly pirates on the field are notified of doing their job. From our Model Driven App (CRM), administrator clicks the “attack” button, and a call is made to an Azure Function API. This then sends a notification to all friendly pirates in the Teams App.
In this workflow, we describe how the attack is actually done
Once the pirate captain receives the notification in the Teams app, he accesses his Canvas app and approaches the target. From the CRM portal, administrators are able to see live data how friendly pirate is moving and enemy pirate in regards to each others position.
Future improvements:
-Embedded reports in the model driven app to limit the different system pirates & captains needs to learn
-Collaborative loot system to build relations with other crews could be created from the mapping systems by including allies in maps and more raids happening
-Pirate dating app
-HR system for gathering LinkedIn information from prospective new pirates and storing it in our database for reporting and easy recruitment