Hip is usually used about things or people when its new, unconventional or non-mainstream. However, hipsters have in modern time become more of a oldschool thing – people dressing up in vintage clothing, listening to old music and living a lifestyle thats is more similar to how it was before (and usually living in the center of Grunerløkka). Being Hip is a thing that is open to interpretation.🤔
Our team has a lot of junior resources – new to the magical world of Power Platform. All of these different functions are considered new and cool – and therefore also hip. And one especially hip and up-and-coming thing is privacy concerns. With everything going digital it is much more important to be aware of security in the solutions: especially in the digital transformation in the Harry Potter Universe: the danger awaits around every turn. Maybe Voldemort somehow find a way to hack into Hermiones app so he is able to locate Harry Potter. This would be catastrophic.
To prevent disaster DLP policies, setting up Audit Logs and Environment-Level Security are some of the important steps that needs to be taken:
- Data Loss Prevention (DLP) Policies help prevent the accidental or unauthorized sharing of sensitive information by controlling which connectors can be used in apps and flows. This ensures that sensitive data remains protected and compliant with regulatory requirements.
- Audit logs track user activities and changes within the Power Platform. They provide a detailed record of actions, which is crucial for monitoring, compliance reporting, and investigating any suspicious activities or breaches.
- Environment-Level Security. Setting up security roles and permissions at the environment level ensures that only authorized users can access specific data and resources. This helps maintain data integrity, protects sensitive information, and ensures that users only have access to the data necessary for their roles.
These are just some of the things that we want to focus on in the further development of our solution.
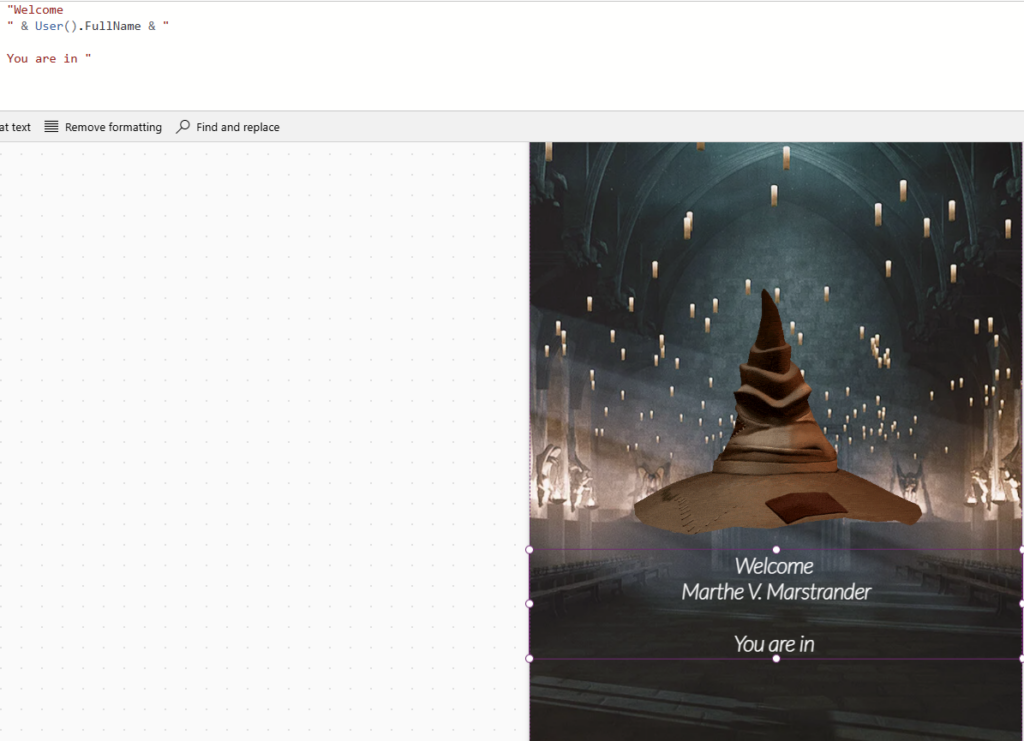
In our app, we have already implemented a secure login process using Microsoft account authentication to ensure your user information is accurately identified and protected.
As shown below, when opening the app: is checks the user credentials and name
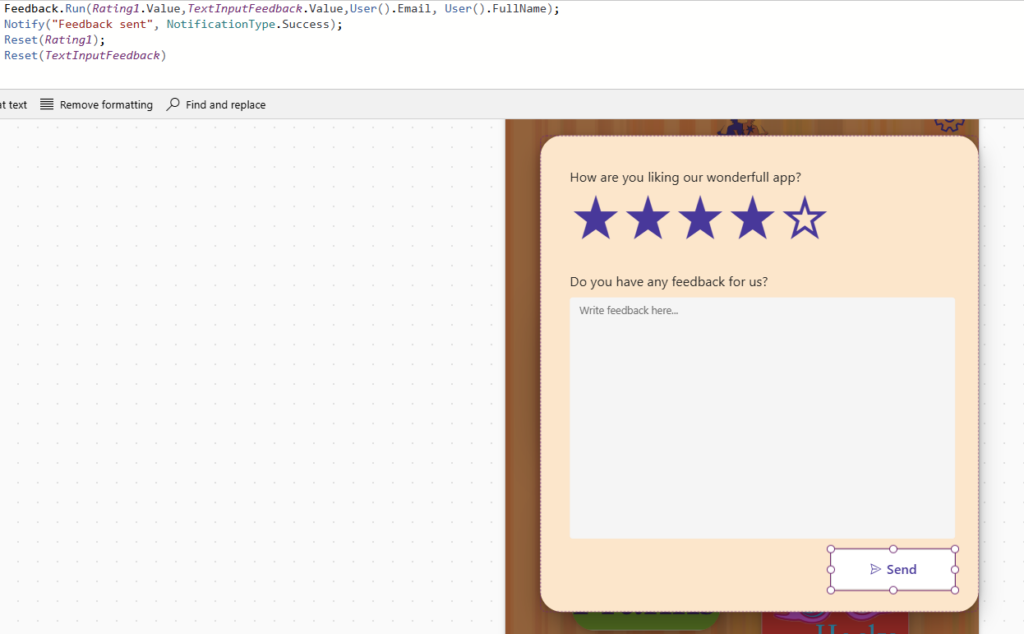
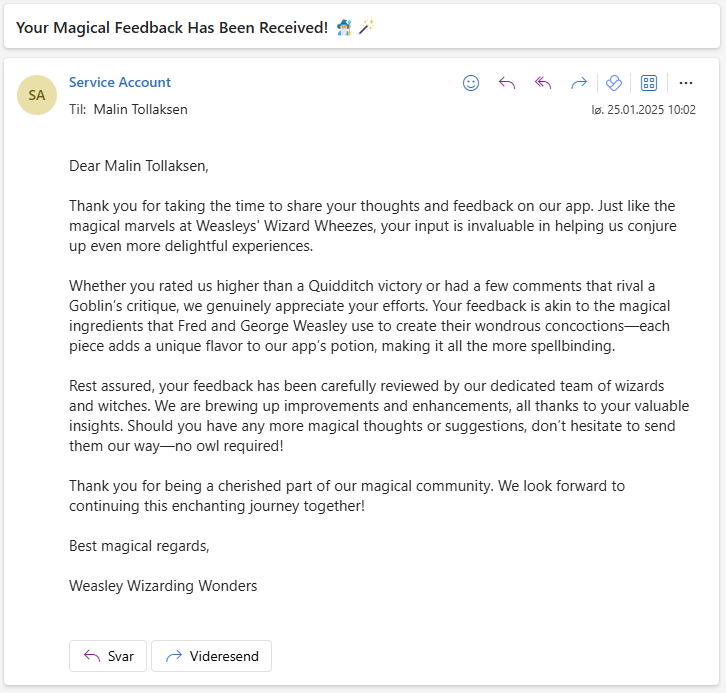
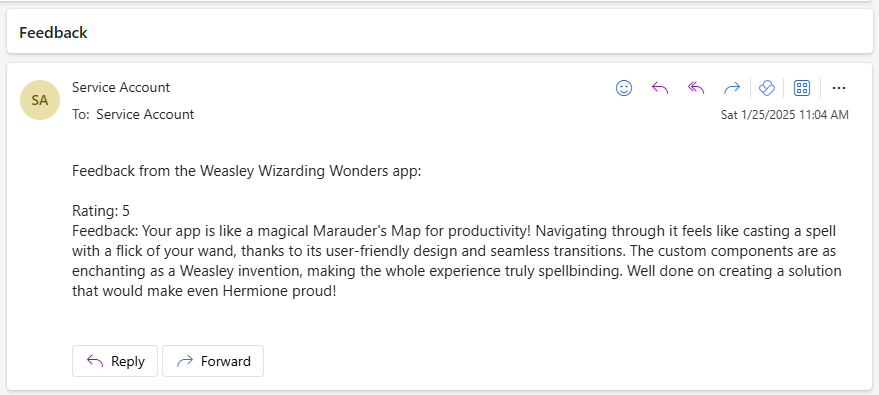
The User Credentials is also used in a feedback flow that provides the oppurtunity to provide the Weasley Twins with feedback on the app. That way, they can continuosly make the app better and more user friendly.
And speaking of cool functions: POWER AUTOMATE
Go with the flow
This is especially magical feature in our app. With the press of a botton it triggers a flow sending out a email through Outlook: The input is dynamic from the users input in the app and dynamic user information gathered as shown above.
Take notice of the tidy and neat code-naming standards following Best Practice.
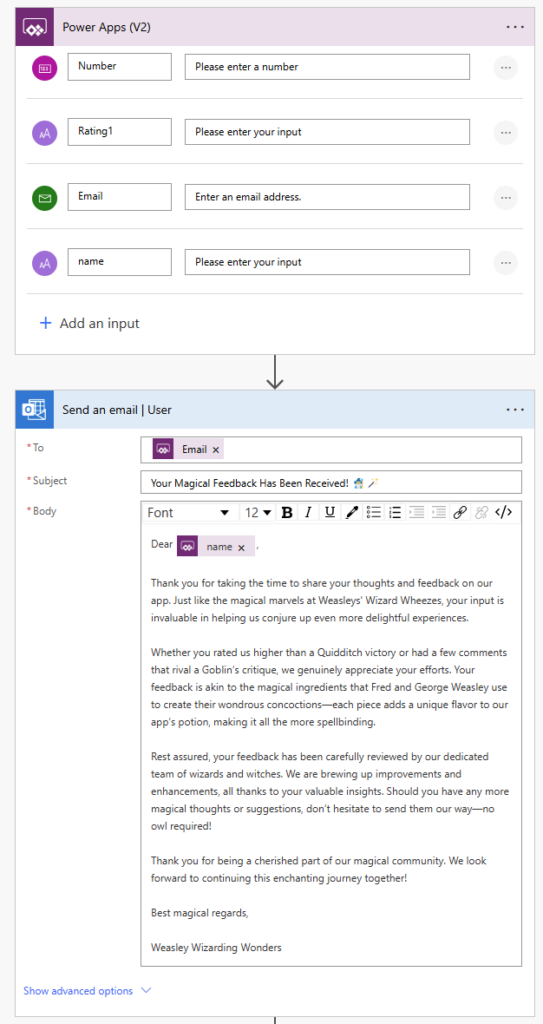
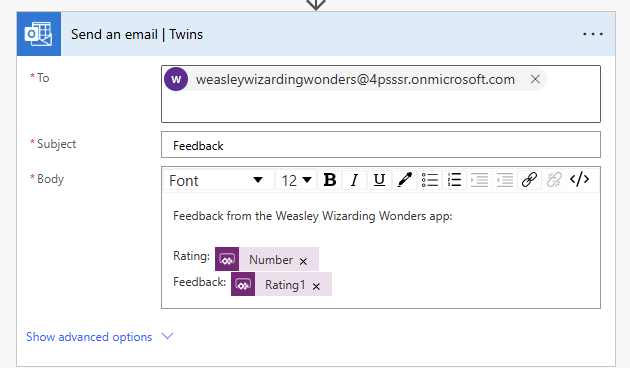
The outcome
To user:
The feedback sent to the twins (service-user):
Keep it HIP and cool, and always go with the flow! 😘
