Microsoft Entra ID Security Groups
To simplify user administration and have better control of user access to the environments, we have created teams of type Microsoft Entra ID security groups.
We created a security group in Entra ID where we add the users we want to give access to the environment.
We then created a team of type Microsoft Entra ID Security Group in Power Platform where we assigned the Entra Group to the team. We then assigned the team the desired security roles:
We now only have to add users to the Group in Entra ID to give access and assign the users security roles.
Power automate – Force Sync users from Entra ID Groups
Now that we have automated and gotten more control of the granting access to users to the environment apps and automations, we need to force sync the users.
The users will not appear in Dataverse unless they have logged into the environment. But building a power automate flow we can solve this issue:
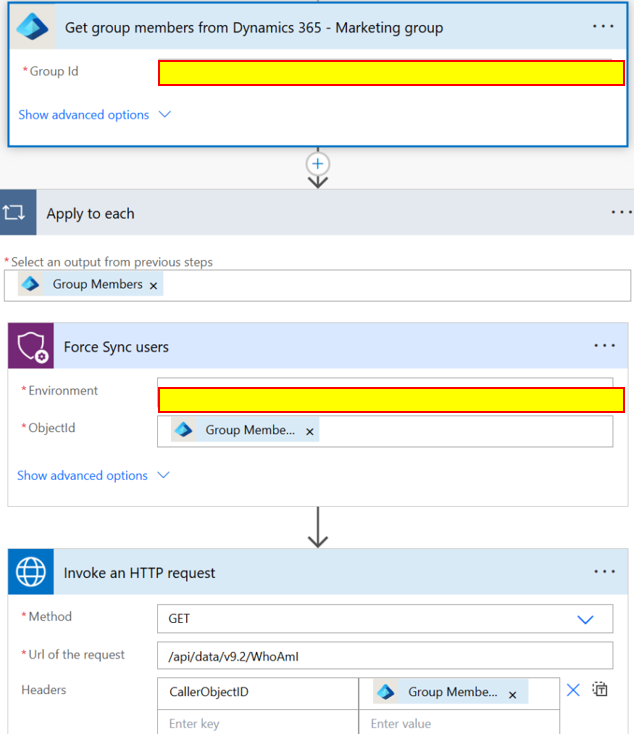
The flow will be triggered once a day and then it will get the members of the Entra ID group. The flow then uses the force sync action to sync the users.
Solution Strategy
The team have created a solution strategy that separates the different types of components in different solutions for easy deploy and a better development process.
Power Platform Pipelines
We have used Power Platform Pipelines to automate the deployment process between environments.